How Does ZK-KYC Work? A Step-by-Step Guide to Private Verification
In the world of Web3, trust is a paradox.
Blockchain technology enables private transactions and decentralized systems, yet most compliant platforms still rely on traditional KYC verification — forcing users to upload passports, driver’s licenses, and personal details into centralized databases.
This creates a dangerous trade-off:
to access financial services, users must expose sensitive data and accept the risk of data leaks, identity theft, and long-term data exposure.
Surveillance fatigue is real, and crypto-native users are right to be skeptical.
Zero-Knowledge KYC (ZK-KYC) introduces a fundamentally different verification process — one that satisfies regulatory compliance while preserving user privacy by design.
This guide explains how ZK-KYC works step by step, how it differs from traditional KYC, and why it represents the future of identity verification.
Why Traditional KYC Verification Fails

Traditional KYC follows a familiar model:
- Users submit personal documents (passport, driver’s license, proof of address)
- Data is stored by a KYC provider, exchange, or financial institution
- Platforms retain ongoing access to sensitive personal information
These databases become high-value targets.
Even with strict access controls, regular security audits, and encryption, centralized KYC systems create structural risk:
- Data breaches expose millions of identities at once
- Users lose control over how long data is retained
- Sensitive information can be reused, leaked, or sold
From a regulatory perspective, this also increases liability for platforms, which must secure and manage personal data indefinitely.
Understanding Zero-Knowledge Proof Technology
Zero-knowledge proof technology changes the foundation of identity verification.
A zero-knowledge proof (ZKP) allows one party to prove a statement is true without revealing the underlying data used to prove it.
A Simple Analogy
Imagine proving you’re over 18:
- Traditional KYC: You show your ID — revealing your name, address, birth date, and ID number
- ZK-KYC: You generate a cryptographic proof that confirms “age ≥ 18” — without revealing any personal details
The verifier receives a valid proof, not actual information.
This cryptographic method enables selective disclosure — proving only what is required, nothing more.
Step-by-Step: How ZK-KYC Works in Practice
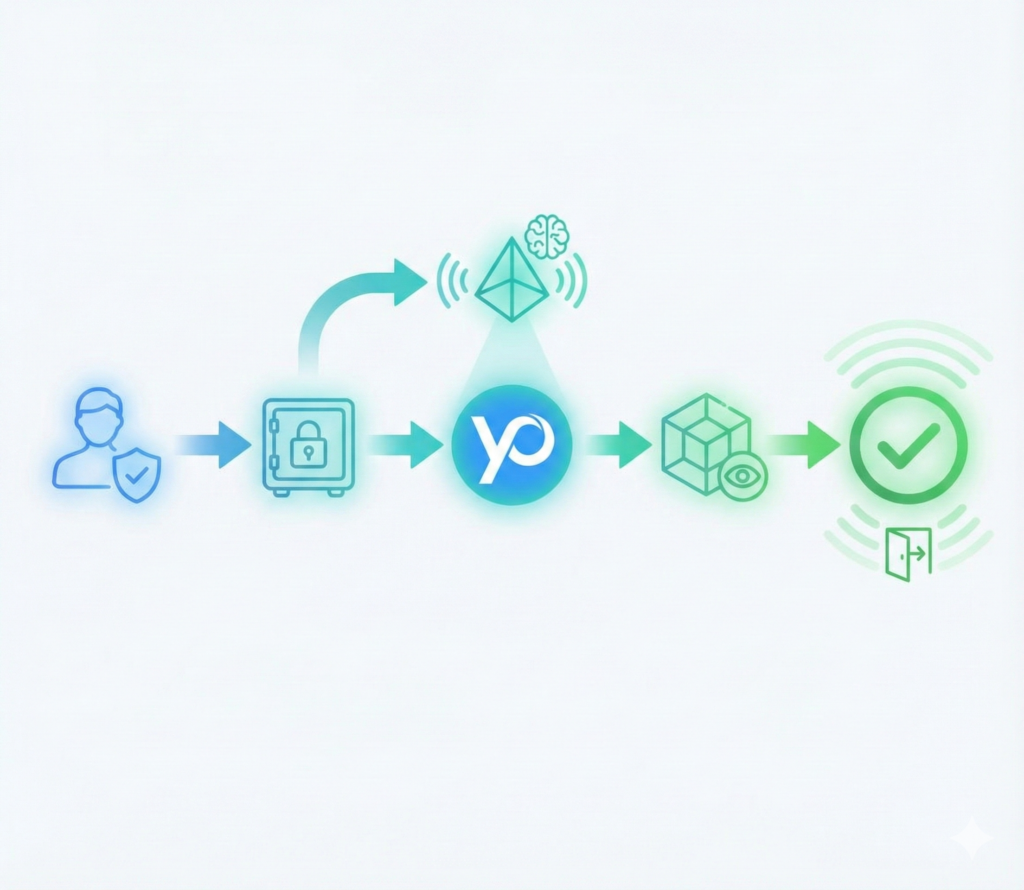
Below is a typical ZK-KYC verification process used by privacy-preserving systems like Verifyo.
Step 1: Identity Verification (Once)
The process begins similarly to traditional KYC, but with a critical difference: data custody.
Users verify their identity using official documents (passport, national ID, driver’s license) and complete liveness checks. This ensures compliance with AML and KYC requirements.
However, the verification logic happens:
- Locally on the user’s device
- Or within a secure, privacy-preserving environment
Raw identity data is not shared with every platform.
Step 2: Encryption & Self-Sovereign Identity
After verification:
- Identity data is encrypted using cryptographic keys
- A self-sovereign identity is created — controlled by the user, not the platform
The underlying data is stored in a secure vault or decentralized storage system, drastically reducing data exposure.
This step is critical for safeguarding user data and maintaining data integrity.
Step 3: Zero-Knowledge Proof Generation
When a user interacts with a dApp or financial institution, the system generates a zero-knowledge proof.
Examples of what a proof can confirm:
- User passed AML and sanctions screening
- User is not from a restricted jurisdiction
- User meets accreditation or age requirements
What the proof does not reveal:
- Name
- Address
- Birth date
- Document scans
The proof confirms compliance without exposing sensitive information.
Step 4: On-Chain Verification
The generated proof is submitted to a smart contract.
Using on-chain verification:
- The smart contract validates the proof’s authenticity
- Verification logic is transparent and immutable
- No personal data is stored on-chain
This allows blockchain technology to enforce compliance without becoming a surveillance layer.
Step 5: Access Granted
Once the proof is verified:
- The platform grants access
- The user remains anonymous
- No sensitive data is retained
This is privacy-preserving KYC in action.
What Platforms Can — and Cannot — See
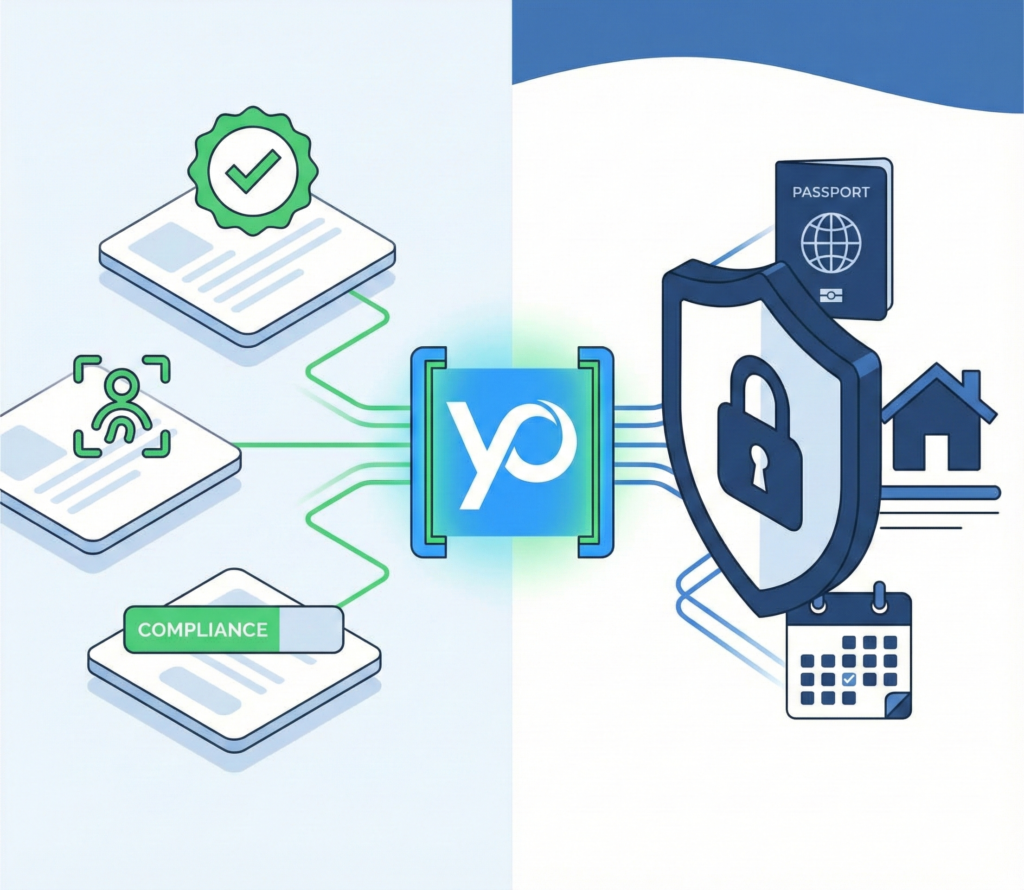
ZK-KYC enables selective disclosure and reduces liability for platforms.
Platforms Can See:
- A cryptographic confirmation (“true/false”)
- Compliance status (AML / sanctions passed)
- Verifiable credentials (e.g. accredited investor)
Platforms Cannot See:
- Passports or driver’s licenses
- Home address or birth date
- Bank statements or healthcare providers
- Underlying identity data
This minimizes data breaches and operational risk.
ZK-KYC vs Traditional KYC: Key Differences
| Feature | Traditional KYC | ZK-KYC |
|---|---|---|
| Data storage | Centralized databases | User-controlled vaults |
| Data exposure | Full documents shared | Zero data revealed |
| Verification process | Repeated per platform | Verify once, reuse everywhere |
| Privacy | Low | High |
| Regulatory compliance | Yes | Yes |
| Risk of data leaks | High | Minimal |
| User control | None | Full |
This comparison will be expanded in our upcoming deep-dive: KYC vs ZK-KYC: Privacy, Compliance, and Risk Explained.
Is ZK-KYC Legal?
Yes.
Regulatory frameworks such as MiCA, GDPR, and global AML directives require platforms to verify users — not to collect excessive personal data.
ZK-KYC aligns directly with:
- GDPR data minimization principles
- Enhanced security requirements
- Maintaining compliance without unnecessary data exposure
From a legal standpoint, zero-knowledge protocols often exceed compliance expectations by reducing systemic risk.
Frequently Asked Questions (FAQ)
What documents are needed for ZK-KYC?
The same documents as traditional KYC (passport, driver’s license, national ID). The difference is how the data is stored and shared.
Can I buy crypto without KYC?
This depends on jurisdiction and platform. Many financial institutions require KYC verification. ZK-KYC allows compliance without sacrificing privacy.
Is ZK-KYC safer than traditional KYC?
Yes. By eliminating centralized storage of sensitive data, ZK-KYC significantly reduces identity theft and data breaches.
Does ZK-KYC work across multiple platforms?
Yes. With verifiable credentials and reusable proofs, users can verify once and access multiple platforms.
Is ZK-KYC compatible with existing systems?
Yes. Zero-knowledge verification layers integrate with existing systems via APIs and smart contracts.
Why ZK-KYC Matters for the Future of Identity
We are moving away from centralized identity systems toward decentralized digital identity.
ZK-KYC represents a shift from data collection to data verification.
For users, this means:
- Privacy
- Fewer repeated verifications
- Reduced risk of data exposure
For platforms, it means:
- Lower operational costs
- Reduced compliance liability
- Enhanced security without storing personal data
Privacy-preserving identity verification is not optional — it is the next evolution of trust in Web3.
Share this content: